A Practical Guide to Streamlining Your Cybersecurity Risk Management Process
- 208 Views
- admin
- 07/18/2024
- Cybersecurity
Conducting a cybersecurity risk assessment is more than just a regulatory checkbox—it’s an essential practice that helps organizations understand their security posture, anticipate threats, and prioritize resources. From healthcare to defense, industries are increasingly required to assess cyber risks not only to meet compliance standards but also to support confident, informed decision-making across teams. Strengthening your cybersecurity risk management process can enhance visibility across your enterprise and help mitigate threats before they become incidents.
Use a Structured Framework to Simplify Risk Management
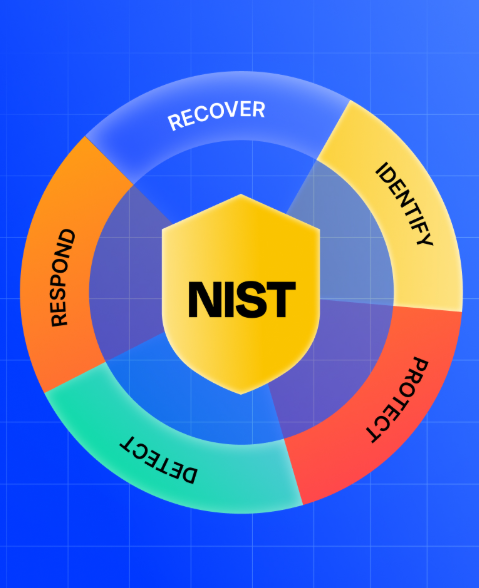
A standardized approach can significantly improve the efficiency of your cybersecurity risk assessments. The National Institute of Standards and Technology (NIST) provides comprehensive guidance through its Special Publications, including SP 800-30, SP 800-37, and SP 800-53. These documents lay out a consistent methodology for managing information system risks across federal and commercial entities.
The Risk Management Framework (RMF) outlined in NIST SP 800-37 focuses on categorizing systems, selecting and implementing controls, and maintaining ongoing oversight. SP 800-30 complements this by detailing how to prepare for, conduct, and maintain risk assessments effectively. Leveraging this framework ensures your process is consistent, repeatable, and aligned with industry standards.
Laying the Groundwork for Your Risk Assessment
Before initiating a cyber risk assessment, it’s crucial to define the purpose, boundaries, and key inputs for the evaluation. NIST recommends the following preparatory steps:
- Define the goals of the assessment
- Determine the organizational scope
- Identify any assumptions or limitations
- Pinpoint sources of risk-related data
- Select analytical methods for assessing risks
These preparatory actions set the stage for a focused and impactful risk evaluation that reflects your organization’s unique environment.
Evaluate Risk Across the Entire Organization
Effective cybersecurity risk assessments should take into account every part of the business—not just IT infrastructure. Threats may arise from vendors, cloud services, physical locations, or outdated software. To achieve meaningful results, you must evaluate systems, applications, and third-party connections that could expose sensitive data.
When applying NIST 800-30’s methodology, it’s essential to clearly define what’s in scope in terms of systems, timeframes, and technologies. Doing so enables a comprehensive understanding of vulnerabilities, attack surfaces, and high-value assets that need protection.
Risk Assessment Is Not a One-Time Task
Technology environments evolve constantly. Whether it’s integrating new applications, onboarding employees, or modifying access controls, changes introduce new risk factors. An effective risk management strategy must be dynamic and continuously monitored.
Staying current means regularly reassessing risks, adapting to emerging threats, and updating controls as needed. It also involves accounting for changes in business processes and educating employees to stay vigilant as risks shift. What was once low-risk could resurface as a new vulnerability if ignored.
Keep Stakeholders Informed Throughout the Process
Risk management doesn’t operate in isolation. It depends on collaboration between technical teams, business leaders, and decision-makers. NIST emphasizes the importance of sharing risk data with key stakeholders such as CISOs, system owners, and program managers.
Maintaining open communication ensures that the assessment reflects accurate operational realities. Stakeholder feedback helps shape effective remediation plans, align security strategies with business goals, and support data-driven decision-making across departments.
Make Your Assessments Actionable and Scalable
For cyber risk assessments to drive real change, they must produce results that are easy to interpret and act upon. Too often, assessments are seen as technical reports rather than strategic tools. Your findings should be digestible, applicable, and tied to business outcomes.
To achieve this, risk assessments should be flexible and tailored to your organization’s size, industry, and risk tolerance. Platforms that align with industry standards—whether NIST CSF, ISO 27001, HIPAA, or others—can streamline the evaluation process and provide unified reporting. This ensures that assessments don’t just check compliance boxes but help guide meaningful improvements to your security posture.
Conclusion
Cybersecurity risk management is a vital process that protects your organization’s infrastructure, data, and reputation. By using structured frameworks, engaging stakeholders, and embracing an ongoing, adaptive approach, you can strengthen your organization’s ability to anticipate, understand, and respond to cyber threats. A streamlined, well-executed risk assessment doesn’t just fulfill compliance—it creates a stronger, more resilient business.
Recent Posts
- How AI is Revolutionizing Architectural Design: A Look at Tools, Trends, and the Future
- Streamlining Cyber Risk Assessments Through Automation
- Understanding the Difference Between Blockchain and Distributed Ledger Technology
- Is Bitcoin Mining Still a Viable Venture in 2025?
- Exploring AI: Unveiling Possibilities, Challenges, and Future Implications